ASPIRE CTF 2021 - Mobile Security CTF
Was pretty bored 🥱🥱😒😒 just scrolling under random tweets on twitter🤳 when i came across this mobile security ctf 🥳🥳….we all love Android ❤️❤️ i mean like, if you don’t, you should, we all should,,,,actually you MUST love Android!!. ASPIRE CTF by Ekraal provided a pretty good recap on some core Android AppSec skills. I joined in solo and commenced smashing the challenges. Below is a detailed walk-through for the challenges that i fought to death.
- Sanity [50pts]
Ahem,,,from the challenge description, it seems like we have two possible approaches to capturing the flag. Well…the simplest would be running strings on the app and using grep to pull out the flag, this would be equal to decompiling the app and looking for the flag in the res or the strings folder but, strings it is.
The other approach would be installing the app and trying to see if we might find the flag, and actually it was spewing the flag .
- Login [150pts]
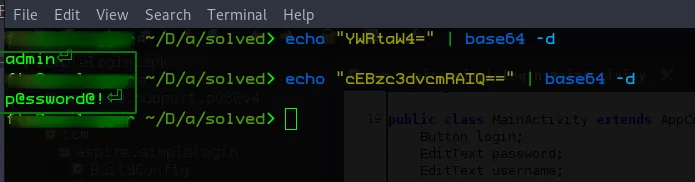
The next challenge was login, this got me thinking like,,, hmmm, we gonna bypass some login screen😲😲 Well, the books taught me that it’s a good practice to have a code review before digging straight into deep thinking, so i used jadx-gui to reverse the application and did a deep probe in the apps MainActivity, found some interesting encoded strings that had been hinted on the challenge description
well, 🤔🤔with the basic coding skills that we have, we can clearly see that this function decodes some embedded Base64 strings and equates them to the strings fed in the UI,,,,,,, hmmm, niice and interesting. so all we have to do is decode the strings and use the flag format in the challenge description, wow.
Pew pew!! we get our second flag and format it accordingly Aspire{admin:p@ssword@!} , that was super sweet .
- Passcode [250pts]
So it seems like we had to do a lot of stuff revolving security, lol. Step 1 as usual was code review, so this particular code drew my attention
seems like it was taking some user input converting it to an integer and equating it to some magic function, well this definitely needed some googling, so i looked up the documentation on class Calendar in java.util.Calendar, got some basic understanding and created the following script to get the passcode.
whoosh, that was one hella job, only to get an ‘incorrect flag”, on re- reading the challenge description , i seems like we had to time travel to june 5th,
Well,i did rewind my pc’’s time to june 5th and boom!! , the key!!
now, transforming the key to the flag was easy as Aspire{706009}. Woot Woot!!
- Preload[300pts]
This one was a bit tricky, haha. So the app name itself was much of a description, so i did some code review, and well well well, see what i found
an embedded sqlite3 databaseso , i could either decompile the app and extract the database, or just install the app and pull the database from the app’s sandbox. Method 1 was quite simple, so i decompiled the app and pulled the database from the database folder.
it appears that everything had been base64 encoded, we can barely read a thing
on decoding the strings, i got some good hints
i got the flag at the 3rd password in the table
- Dropper [300pts]
So they decided to kill us all with an extension less file, challenge accepted. exiftool said it was an Android shared library, so i appended a .so extension and launched ghidra to do some static analysis…..potato potayto!!
i loaded ghidra with the library and commenced static analysis
from the decompiled c pseudo code, we can already see that the function compares the password input to the predefined variables and pops a shell if they match, so i decoded the variables from hes to ASCII and got the flag
i used python3 console to decode the hex, was too tired to create an automation script 😫 Aspire{adm1_AB0T}
- Firebase [500pts]
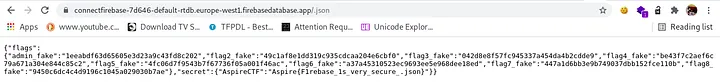
well, this one was quite simple and sweet so i decompiled the application, and grepped for ‘firebase” in the strings.xml file, then narrowed down the search to get the firebase url
appending .json to the firebase url basically leaks the stored data if the app is vulnerable to firebase misconfiguration, so i did just that and got hold of the golden flag
i used curl and piped the output to grep to get the exact flag,
This is where we part ways friend, i really enjoyed the game and i wish more like these come my way,,,,anyways i had been used to x86 assembly but this ctf opened my eyes on the advantages and the great use of ARM assembly, here are some recommended good reads Writing ARM Assembly (Part 1) Welcome to this tutorial series on ARM assembly basics. This is the preparation for the followup tutorial series on
INTRODUCTION TO ARM ASSEMBLY BASICS
and
by the end of those two, you should be a leet, pro jedi master on arm assembly and exploit dev……see you in the next good stuff, have fun 🥳🥳 ……am off to take some water.






















Comments powered by Disqus.